Bluetooth Low Energy (BLE) spam, often referred to as Bluetooth LE spam APK, has emerged as a significant issue in today's digital landscape, especially given the extensive adoption of Bluetooth technology across a multitude of devices. This article aims to explore the essence of BLE spam, examine its various impacts, and discuss effective ways to address and reduce its occurrence.
Information about Bluetooth Le Spam
| Tên | Bluetooth Le Spam |
|---|---|
| Update | |
| Compatible with | Android 6.0 + |
| Version | 1.0.5 |
| Capacity | 8 M |
| Category | tools |
| Developer | Bluepixel Technologies |
| Price | Free |
| Path to Play Store |
About Bluetooth Le Spam
Bluetooth Low Energy (BLE) Spam, a new digital concern, arises from the misuse of the power-efficient Bluetooth 4.0 technology, primarily used in IoT and smart devices. This form of spam involves unsolicited transmission of data to devices within range, often in public spaces with high device density. It poses significant privacy concerns due to potential user tracking without consent, security risks through malicious prompts leading to device compromise, and user annoyance due to continuous unwanted messages disrupting device functionality.
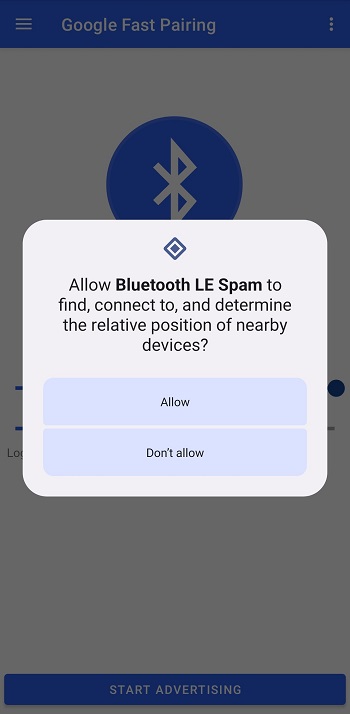
To mitigate BLE Spam, a combination of user awareness, device-level solutions, regulatory measures, and advanced security protocols is essential. Educating users about the risks of unknown Bluetooth connections, incorporating features in devices for blocking unwanted requests, and setting regulatory standards to control BLE misuse are crucial steps. As Bluetooth technology evolves, future measures may include more robust security features and the use of AI and machine learning for automatic spam detection and prevention, aiming to balance the benefits of BLE with the need for security and user privacy.
Understanding Bluetooth Low Energy (BLE) APK
Introduced with the Bluetooth 4.0 core specification, BLE APK stands out as a power-efficient iteration of the traditional Bluetooth standard. Tailored for devices requiring the transmission of small data quantities over distances up to 100 meters, it achieves this with substantially lower power consumption than its classic counterpart. This efficiency has propelled BLE's popularity, especially in the realms of IoT (Internet of Things) devices, wearable technology, and smart home appliances.

The Emergence of BLE Spam Latest Version
BLE spam involves the unsolicited transmission of data packets to Bluetooth-enabled devices within range. It typically occurs in public places with high foot traffic, such as shopping malls, airports, or busy streets, where the density of Bluetooth-enabled devices is high. Advertisers or malicious entities can exploit BLE to broadcast unwanted messages or prompts, often in an attempt to redirect a user to a particular website or advertisement.
Implications of BLE Spam
Privacy Concerns: BLE spam can potentially be used to track individuals by repeatedly sending them unique identifiers. This tracking can occur without the user's consent, raising significant privacy issues.

Security Risks: Malicious BLE spam APK can pose security risks. For example, if a user inadvertently accepts a malicious prompt, their device could become compromised.
User Annoyance and Device Disruption: Constant spam messages can be a significant annoyance to users. Moreover, these unsolicited messages can disrupt the normal functioning of Bluetooth-enabled devices, leading to a poor user experience.
Mitigating BLE Spam for Android
User Awareness and Education: Educating users about the risks associated with accepting unknown Bluetooth connections is vital. Awareness campaigns can inform users about how to recognize and avoid BLE spam.
Device-Level Solutions: Smartphone and device manufacturers can incorporate features that allow users to easily block or filter BLE requests. For example, options to auto-reject requests from unknown devices can be helpful.
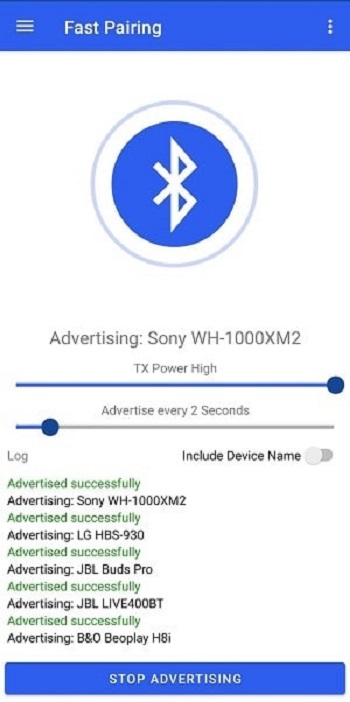
Regulatory Measures: Governments and regulatory bodies can play a role by setting standards and regulations to control the misuse of BLE for spamming purposes.
Advanced Security Protocols: Implementing advanced security protocols and encryption in BLE communications can reduce the risk of malicious spam.
The Future of BLE and Spam Prevention
As BLE continues to evolve, so do the strategies to combat spam. Future iterations of Bluetooth technology may include more robust security features to prevent unauthorized data transmission. Additionally, AI and machine learning could be employed to better detect and block BLE spam automatically.
In Conclusion
While BLE spam presents challenges in terms of privacy, security, and user experience, concerted efforts from users, industry players, and regulatory bodies can help mitigate its impact. The evolution of Bluetooth technology towards more secure and user-friendly iterations will also play a crucial role in addressing these concerns.








.jpg)

Your rating